Showing 1 - 6 of 6
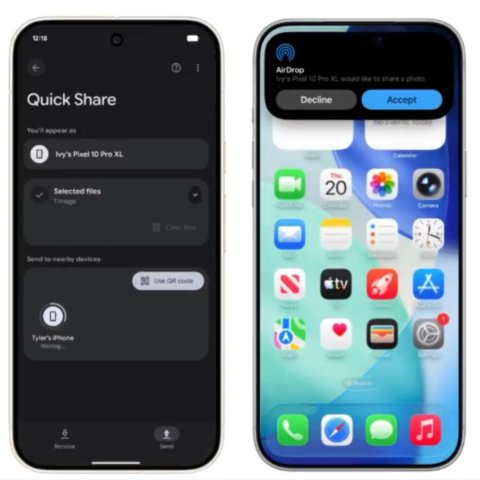
Google confirms Android Quick Share will soon work with AirDrop
Life, Puriward Sinthopnumchai, Published on 08/02/2026
» Google has officially confirmed that its Quick Share feature will soon allow Android users to transfer files directly to Apple’s AirDrop, expanding a capability previously thought to be exclusive to the Pixel 10 series.
Microsoft issues emergency Office update to fix zero-day flaw
Life, Puriward Sinthopnumchai, Published on 04/02/2026
» Microsoft has released an out-of-band emergency security update to address a zero-day vulnerability in Microsoft Office that is being actively exploited, extending support for affected versions through 2026.
Game platform Steam to end support for system 32-bit Windows
Life, Puriward Sinthopnumchai, Published on 24/12/2025
» Valve has officially announced the end of support for 32-bit Windows operating systems, following a recent update that transitions the Steam Client to a native 64-bit architecture to enhance security and performance.
Japanese game firm makes applicants draw live to prevent AI-made portfolios
Life, Puriward Sinthopnumchai, Published on 06/12/2025
» A mid-sized Japanese video game developer has introduced a mandatory live drawing test for job applicants to screen out those relying on generative artificial intelligence (AI).
Google warns new AI-powered malware thinks and rewrites its own code
Life, Puriward Sinthopnumchai, Published on 17/11/2025
» The Google Threat Intelligence Group (GTIG) has released a report detailing a significant shift in cybersecurity, noting that hackers are no longer just using AI for assistance or writing code but are integrating it into malware.
Microsoft restricts IE mode after hackers exploit zero-day flaw
Life, Puriward Sinthopnumchai, Published on 14/10/2025
» Microsoft has tightened access to Internet Explorer (IE) mode in its Microsoft Edge browser after discovering that hackers were exploiting a critical zero-day vulnerability to take control of users’ computers.